Overview
Cyolo Core Components
Identity and Access Controller (IDAC)
- Cyolo's core engine, deployed within the customer’s network close to the resources (e.g., servers, applications, databases) that the organization wants to secure and provide access to.
- Operates as an inverse proxy, dynamically brokering secure connections between users and the resources they are authorized to access. This ensures that sensitive data remains within the trusted network and does not traverse through untrusted environments.
- The IDAC facilitates interactions with external services (e.g., SMS gateways, GitHub) to enable features such as MFA. Note, however, that these interactions are exclusively handled through the IDAC gateway.
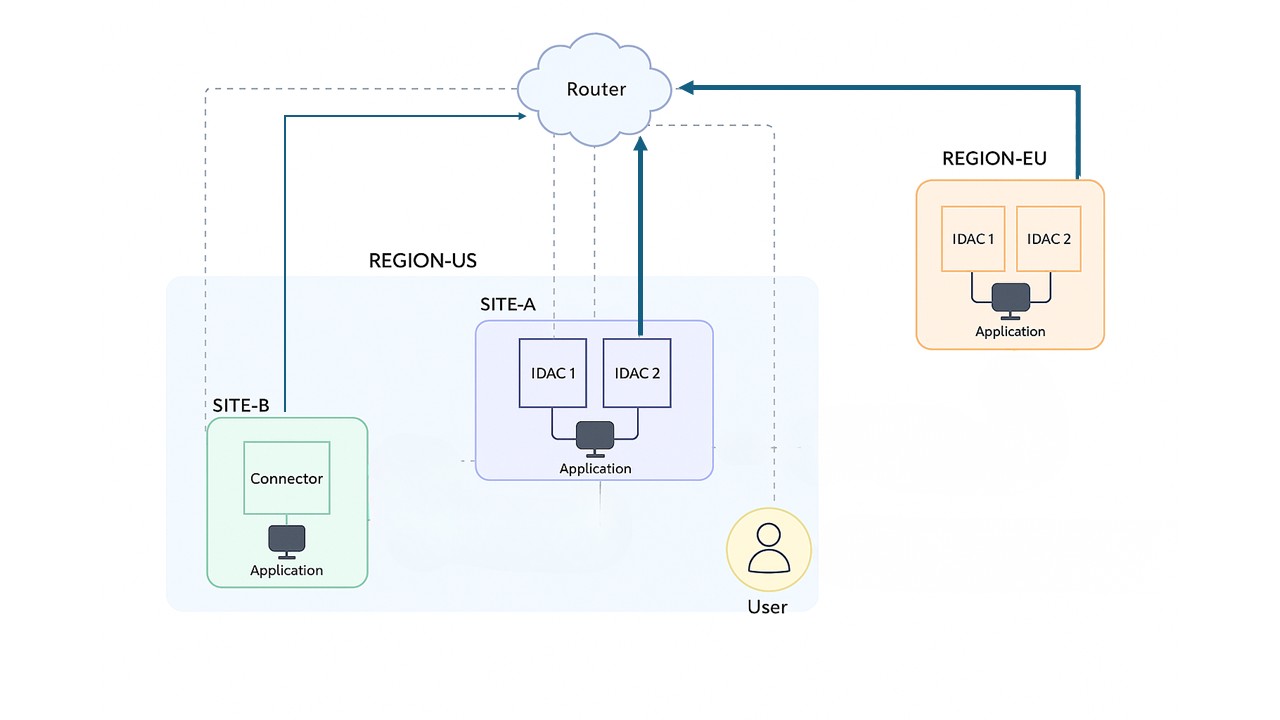
Connector
- Cyolo Connector is a stateless software component deployed within the network that functions as a proxy to protected assets without exposing them directly to external networks. Each Connector is part of the customer's Tenant, working alongside the IDACs.
- The Connector must communicate with Cyolo Global Gateway (CGG) or Private Gateway (PG). Any communication to the Connector also goes through the IDAC, via CGG/PG.
Comparison to IDAC
- Lower Resource Requirements: 2 CPUs, 2GB RAM, 20GB (compared to IDAC)
- Stateless design provides simpler maintenance and upgrade
Considerations
Using a Connector introduces an additional network hop in the communication flow: User → ... → IDAC → [Router → Connector →] Application
- For best performance, deploy 1-2 IDACs regionally close to the Connector. Otherwise, users near the resource will experience longer travel distances.
- Guacamole and rdp-proxy can only run on a regular IDAC. For applications accessed through the Connector, the Connector will use any guacamole and rdp-proxy available in the tenant.
Cyolo Global Gateway
- Managed by Cyolo and deployed on the public cloud (AWS and Google), across multiple global zones.
- Serves as a secure entry point for users to access the Cyolo system - removing the need for organizations to maintain their own gateways.
Private Gateway
- Customer-managed gateway that can be deployed in any location the organization chooses - such as on-premises, in a private cloud, or at an edge location.
- Acts as a dedicated entry point to the Cyolo system - tailored to meet the organization's specific security, compliance, and infrastructure needs.
Site
- Logical entity that groups IDACs within the same network - facilitating resource segmentation and enhancing security.
- Customers can have several sites, allowing for flexible and scalable management of resources across different network boundaries.
- When publishing applications, administrators select the relevant sites to determine resource accessibility and apply specific policies or configurations, as needed.
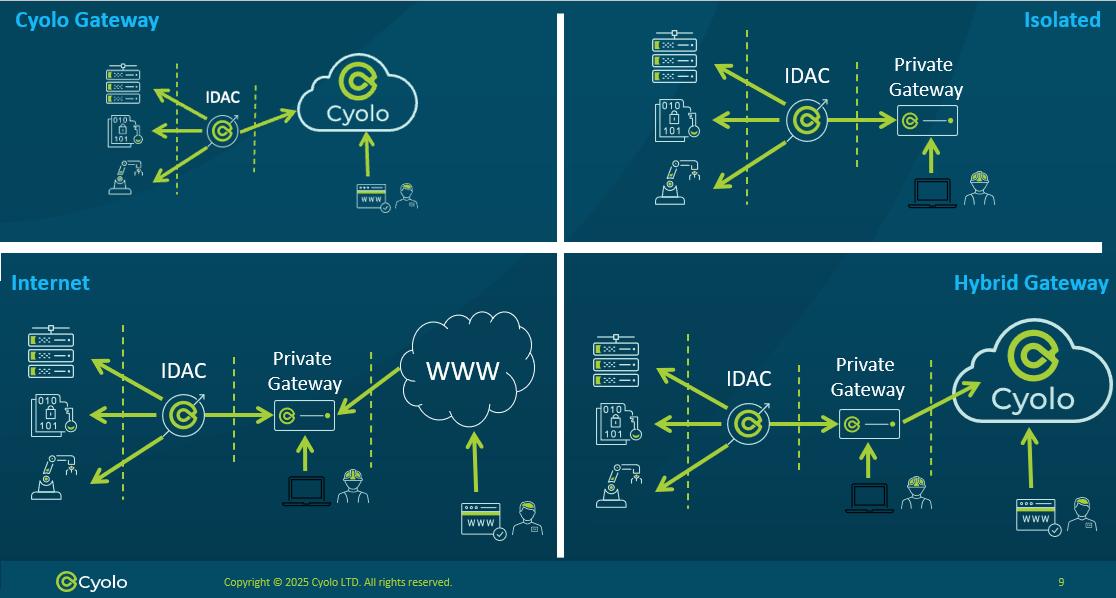
Deployment Models
The Cyolo system consists of four flexible deployment models:
- Cyolo Gateway - IDACs communicate through the Cyolo Global Gateway (CGG), a managed entry point for users to access the Cyolo system. Users can securely access the system if they can access one of the CGG instances deployed worldwide.
- Isolated - IDACs communicate exclusively through Private Gateways (PGs). Users can access the Cyolo system only through one of the PGs controlled and managed by the customer.
- Internet - IDACs communicate through PGs that are accessible from the internet. Users can access the Cyolo system if they have internet connectivity.
- Hybrid Gateway - IDACs communicate through PGs, but these gateways themselves are connected to the CGG. Users access the Cyolo system by connecting to the CGG, which serves as the upstream entry point for the PGs.
Updated 27 days ago