Assigning Identities, Supervision, and Rules to Applications
Identities
This section allows the portal admin to configure who can access the application. The drop-down has the following options:
- None –
- Anonymous identities – Anyone in possession of the application URL can connect to the application without authentication.
- Any authenticated identity – Any user logged in to the Applications Portal can connect to the resource.
- Specific identities – When this option is selected, click the search box to select the users, user group, or API keys from their respective tabs. For more information on configuring users, refer to How to Create Users or How to Create User Groups.

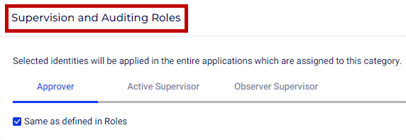
Supervision and Auditing Roles
Cyolo offers a feature called supervised access, which is used when a user's access must be approved by a supervisor before connecting to any resource. The supervisor not only approves the access beforehand but can also monitor the session in real time.
This section has the following options to configure:
- Approver - Approvers can grant or deny access to applications and terminate authorized sessions.
- Active Supervisor - Active supervisors can join ongoing sessions interactively and terminate authorized sessions.
- Observer Supervisor - Observer supervisors can join ongoing sessions non-interactively and terminate authorized sessions.
- Auditor - Auditors can replay recordings of application interactions. Auditing is not supported in web applications and SSH tunnel applications.
- To use the approvers, active supervisors, observer supervisors, and auditors set on the respective pages under the Roles menu, enable the Same as defined in Roles checkbox. This is enabled by default. To set users or user groups other than those defined under Roles:
- Uncheck Same as defined in Roles.
- Click the search box and select user groups from the Groups tab and users from the Users tab.
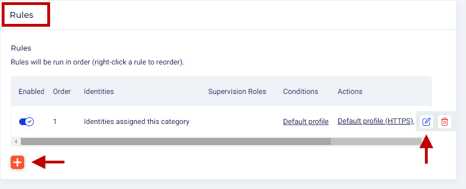
Rules
Rules are a combination of identities, conditions and actions profiles. For users to gain access to applications, they must fulfil all the conditions and requirements set forth in these features.
If the application is part of a category, the application inherits the rules configured within the category. If additional rules must be created, follow these steps:
- Click the + symbol to create a rule.
- More than one rule can be defined here. When more than one rule is created, they are enforced in the order created. To re-order the rules, right-click and move them up or to the top.
- Default properties of rules when created here:
- The identities set in this rule are the same as in the Identities section above.
- The conditions defined in this rule are those in the default Conditions profile created on the Conditions page.
- Based on the type of application, the default action profile is defined in this rule. For example, if the application type is RDP, the profile will be the default profile of the application - Default profile (RDP).
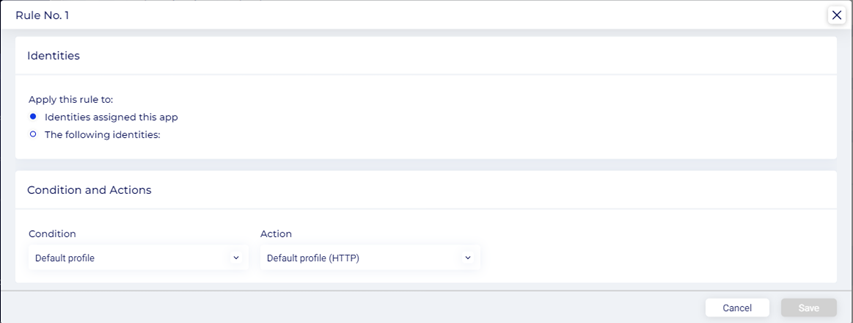
● To change the default properties, edit the rule.
● Select the rule and click the Edit button.
● In the Rule window, the default selection under Apply this rule to is Identities assigned this category.
● Select the The following identities radio button to set identities here.
● Click the Select identities drop-down and select the options displayed here. The steps to select are identical to that described in the Identities section above.
● Click the drop-down under Conditions to change the default profile to a custom profile. Custom profiles, if created on the Conditions page, are listed here. Click the Create new condition to create a new Conditions profile. For more information on Conditions, refer to the section: Conditions.
● Click the drop-down under Actions to change the default profile. Custom profiles, if created on the Actions page, are listed here. Click the Create new action to create a new Action profile.
For more information on Actions, refer to the section: Policy Actions.
Updated 2 months ago