Policy Actions
Overview
Once a user is successfully authenticated and has met the conditions outlined in the conditions profile, the portal admin can configure the actions the user is permitted to carry out when connected to the remote application or server. Beyond specifying the actions that a user can or cannot carry out, the portal admin can also enforce actions carried out by the Cyolo platform.
About Actions
- Actions are created as profiles on the Policies > Actions page of the Cyolo admin portal.
- The Actions page is pre-populated with default action profiles for each application type or protocol. These profiles cannot be deleted but can be edited. When configuring applications, the default profile for the respective application type or protocol is added to the rule. This can be changed to a custom profile.
- Each profile includes actions specific to an application type or protocol.
- An Actions profile can be defined either within an individual application or at the category level.
- Multiple custom Actions profiles can be created, each designed for a specific purpose.
Configuring Actions Profile
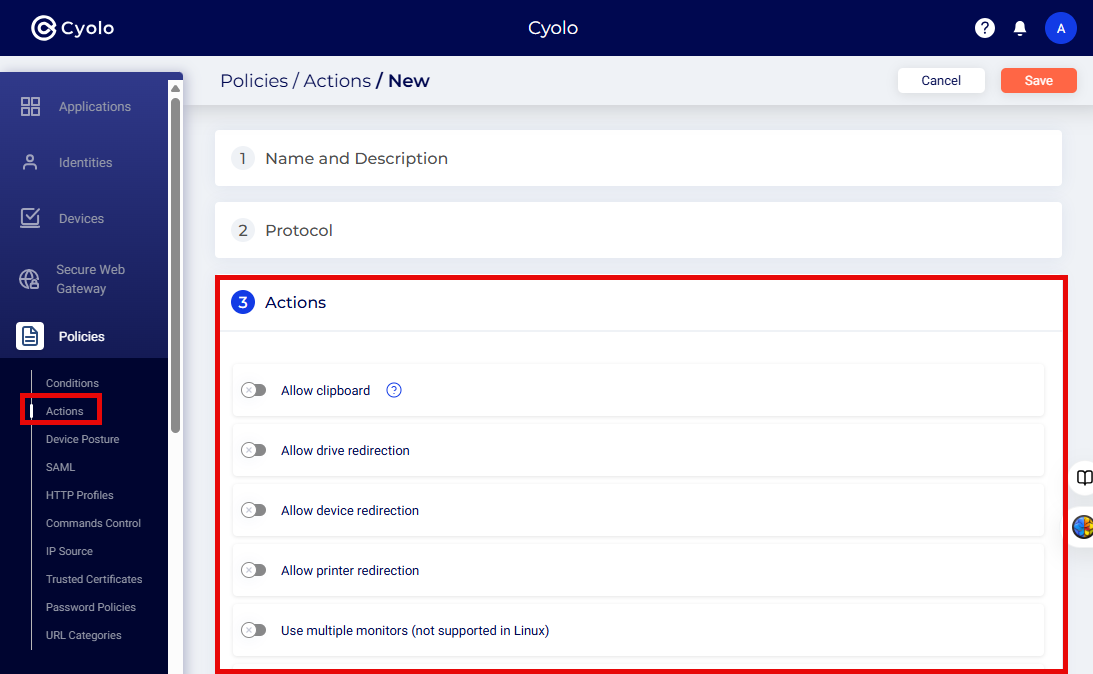
Creating a New Policy Action
Options for HTTP, HTTPS, SMB
The following options apply to HTTP, HTTPS, and SMB:
- Disallow file uploads: Prevents file upload to a folder or directory. This option is not enabled in the respective default profiles.
- Disallow file downloads: Prevents the user from downloading files from a folder or directory. By default, this option is not enabled.
Options for RDP, SSH, VNC, TELNET
The following options apply to RDP, SSH, VNC, and TELNET:
- Allow clipboard: Enabling this option allows copy, paste and other clipboard operations when using the native clients of RDP, SSH, VNC, and TELNET.
- Record session: This option enables recording of the remote access session. This option is disabled by default.
- Supervisors can join the application's active sessions: Enabling this option allows the designated supervisor of the user to join the remote access session. This is disabled by default.
Options for RDP
The following options apply to RDP:
- Allow drive redirection: Enabling this option allows users to access files and folders stored on their local drives from within the RDP session. This option is disabled by default.
- Allow device redirection: Same as above but for locally connected devices. This option is disabled by default.
- Allow printer redirection: Same as above but for printers. This option is not enabled by default.
- Use multiple monitors (not supported in Linux): This option enables users to extend their remote desktop session across multiple monitors, rather than being limited to a single screen. This option is disabled by default.
- Allow camera: This option enables the local camera to be used in the remote desktop session. This is disabled by default.
- Allow audio input: Same as above but for audio input.
- Allow COM redirection: This option enables access to the local COM port by applications running in the RDP session. This option is disabled by default.
- Allow smart card redirection: Enabling this option allows smart cards to be used in the remote session. This is disabled by default.
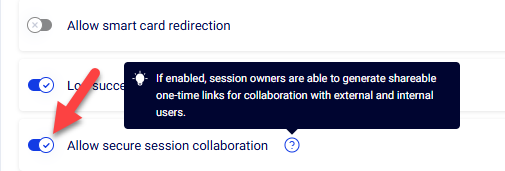
- Allow secure session collaboration - When enabled, session owners are able to generate shareable one-time links for collaboration with external and internal users. Note: A maximum of three collaboration links can be generated per session.
Options for SSH
The following options apply to SSH:
- Allow port forwarding: This option allows the user to securely redirect network traffic from a local port on their machine to a remote port on a remote server through the SSH connection. This is disabled by default.
- Allow x11 forwarding: This option allows the user to run graphical applications on a remote server and display them on their local machine in a SSH connection. This is disabled by default.
- Commands Control: This option allows the user to add a list of allowed or denied commands.
Options for SMB
The following options apply to SMB:
- Enhanced logging: This option is applicable to SMB applications, where SMB sessions are logged with additional information.
- Anti-malware scan: Enable this option to run anti-malware scan on the files uploaded and downloaded during an SMB session. The anti-malware service integration is configured on the Integrations > Anti Malware page.
Options for SWG
The following option applies to Secure Web Gateway (SWG):
- Block URL categories: Enable this option to block specific URL categories. For more, see Secure Web Gateway.
Options for HTTP, HTTPS, SaaS, Link, SSH Tunnel, RDP, SSH, VNC, TELNET, and SMB
The following options apply to HTTP, HTTPS, SaaS, Link, SSH Tunnel, RDP, SSH, VNC, TELNET, and SMB protocols:
- Log successful user access: Enable this option to log successful logins. This option is by default enabled in default profiles.
- Enforce session fingerprinting: Session fingerprinting creates a unique identifier of a user's session by collecting information such as device type, device model, OS, and OS version - among other attributes, when the user logs in to the portal or connects via Cyolo Connect. When this option is enabled, the user session is fingerprinted, requiring users to access resources only from the previously used device, thereby preventing unauthorized access.
Options for RDP, SSH, SSH Tunnel
The following option applies to RDP, SSH, and SSH Tunnel:
- Native session access token will be valid for (minutes): This option configures the amount of time the user has to log in to an RDP or SSH server using their respective clients after clicking on the application icon on the Application Portal. By default, this is set to 30 minutes. This option is enabled by default.
Options for HTTP, HTTPS
The following option applies to HTTP and HTTPS:
- Web Application Firewall (WAF): This option blocks and/or reports web application security vulnerabilities and exploits based on predefined rules. These rules are configured on the Policies > HTTP Profiles page. While a default profile is available, admins can create custom rules as needed. Portal admins have two choices:
- Report: Selecting this option will log vulnerabilities without taking action to block them.
- Block: This option will actively block vulnerabilities to prevent exploitation and log them.
RDP Action Policies
Web RDP | Native RDP | |
|---|---|---|
Allow clipboard | + | + |
Record session | + | + |
Supervisors can join the application's active sessions | + | _ |
Native session access token will be valid for (minutes) | _ | + |
Max session duration (minutes) | + | + |
Allow drive redirection | _ | + |
Allow device redirection | _ | + |
Allow printer redirection | _ | + |
Use multiple monitors (not supported in Linux) | _ | + |
Allow camera | _ | + |
Allow audio input | _ | + |
Allow smart card redirection | _ | + |
Note- RDP Known Limitations
In Web sessions, Cyolo can limit access to specific native apps. However, in native mode it cannot.
Updated 3 months ago