Vault
Types of Vaults
The Cyolo Vault feature provides a secure method to store, manage, and retrieve confidential information, such as passwords, API keys, and certificates. These stored secrets enable end users to sign in to servers and applications seamlessly in the background without having to enter the credentials or even know the credentials. Additionally, Cyolo Vault ensures that only authorized users or API keys can retrieve stored secrets. Another salient feature of the vault is password rotation where passwords of LDAP users are periodically changed at set intervals.
- System Vault: The system vault stores usernames and passwords, private keys, API keys, and certificates set by the Cyolo administrator on the Vault > Secrets page of the admin portal. End users, when accessing a resource, do not need to know the credentials to sign in to the resource. If the option Assign secret from vault is set as the authentication method for an application, end users are not prompted for credentials; instead,
the stored secret is used to automatically sign in the user. Administrators can create, update, or delete information in the system vault via the admin portal. - Personal Vault: Similar to the system vault, the personal vault is designed to store end user credentials. The difference is that these credentials are stored only when the option Prompt user and store in personal vault is set in the application's Authentication Method section. When this option is set, the user will be prompted for username and password when connecting for the first time. The entered credentials will be stored in the user's
personal vault and automatically used for every subsequent sign-in attempt, and the user will not be prompted for credentials thereafter. Unlike the system vault, users cannot export or view the secrets. The secrets stored in the personal vault of a user can be viewed on the Cyolo Application Portal under User Secrets.
Components of the Cyolo Vault Secrets
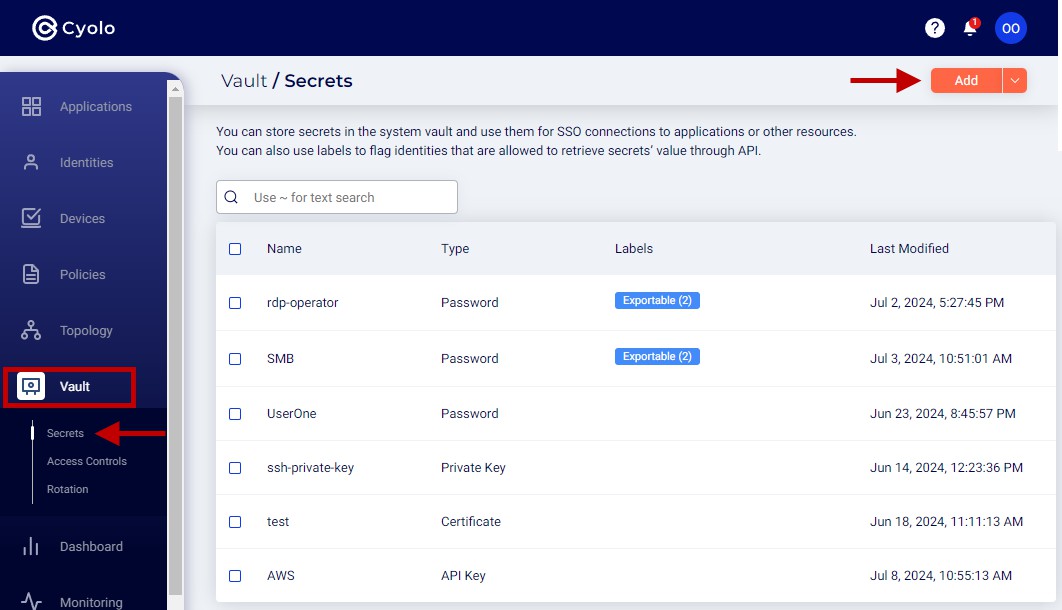
Within the Cyolo platform, the term secret refers to the confidential information stored on the Secrets page under the Vault menu on the admin portal.
-
The vault supports various types of secrets. Each type has fields according to the nature of the information stored.
-
Admin users can add, edit, and delete secrets on the admin portal. Labels can be applied to secrets for better organization and retrieval.
-
Confidential information such as passwords, private keys, and API key secrets cannot be viewed on the admin portal.
-
Similarly, end users can view some of the non-confidential parts of secrets on the Cyolo Application Portal, but cannot edit or delete them.
-
Admins with the necessary permission can retrieve the secrets by exporting them using the API.
Types of Secrets
-
Passwords: The admin portal can add usernames and passwords of resources, each identified by a name, called Secret name on the portal. While the username is visible on the portal, the password is not.
-
Private Keys: Private keys are part of a key pair used for identity verification when connecting to a server, such as SSH. Private keys are added with a name, username, and the private key. The private key is not visible on the portal.
-
API Keys: API keys serve to identify and authenticate applications or users. These are stored in the combination of name, keyID, and key secret. They are stored exclusively in the system vault. The key secret is not visible on the portal.
-
Certificates: Certificates, when used to sign in to servers, are primarily used for client authentication when the server requires mutual authentication of both client and the server (mTLS). On the Secrets page, the public key and private key are stored separately in PEM format. While the public key is visible, the private key is not visible on the admin portal.
-
Generic Secrets: These are strings of characters used for simple authentication. The secret consists of two strings, a name, and a value. The secret is not visible on the admin portal.
To configure secrets, refer to the section: How to Configure Secrets.
Access Controls
Access Controls in Cyolo Vault determine who can export the secrets and retrieve the confidential information within.

-
Administrators can define the users, user groups, or API keys that can export each secret. Alternatively, one or more secrets can be grouped under a label; users with permission to export them can then be assigned to them.
-
Access controls can be based on roles, users, or user groups.
-
Access controls can be labelled with a name and a colour for better organization.
To configure access control, refer to the section: How to Configure Access Control.
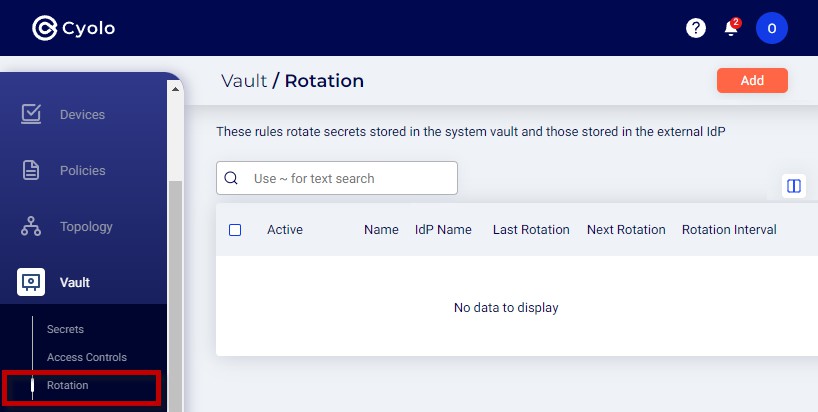
Rotation
The Rotation feature in Cyolo Vault allows administrators to configure rules for automatic rotating of LDAP passwords that are stored in the system vault at set intervals. For this configuration to work, the LDAP server must be integrated into the Cyolo platform.
-
Rotation of secrets applies to passwords only.
-
An LDAP server must be integrated to the Cyolo platform as external Idp on the Integrations > Identity Providers page before configuring this feature.
-
The LDAP server must have the user account for which the password is being rotated.
-
The configuration will rotate the corresponding LDAP password.
-
Rotation rules can be configured to rotate passwords automatically at specified intervals.
-
The password policy on the LDAP server must be at least as strong as the password policy on the Cyolo platform. For example, if the LDAP server requires a password with at least one uppercase letter, one lowercase letter, one special character, and one number, the password policy in the Cyolo admin portal must match this strength.
For more information on password policies, refer to the section: How to Create a Password Policy.**
To configure Rotation, refer to the section: How to Configure Password Rotation.
Updated 7 months ago