Commands Control (COPY)
Commands control allows users to add a list of allowed or denied commands.
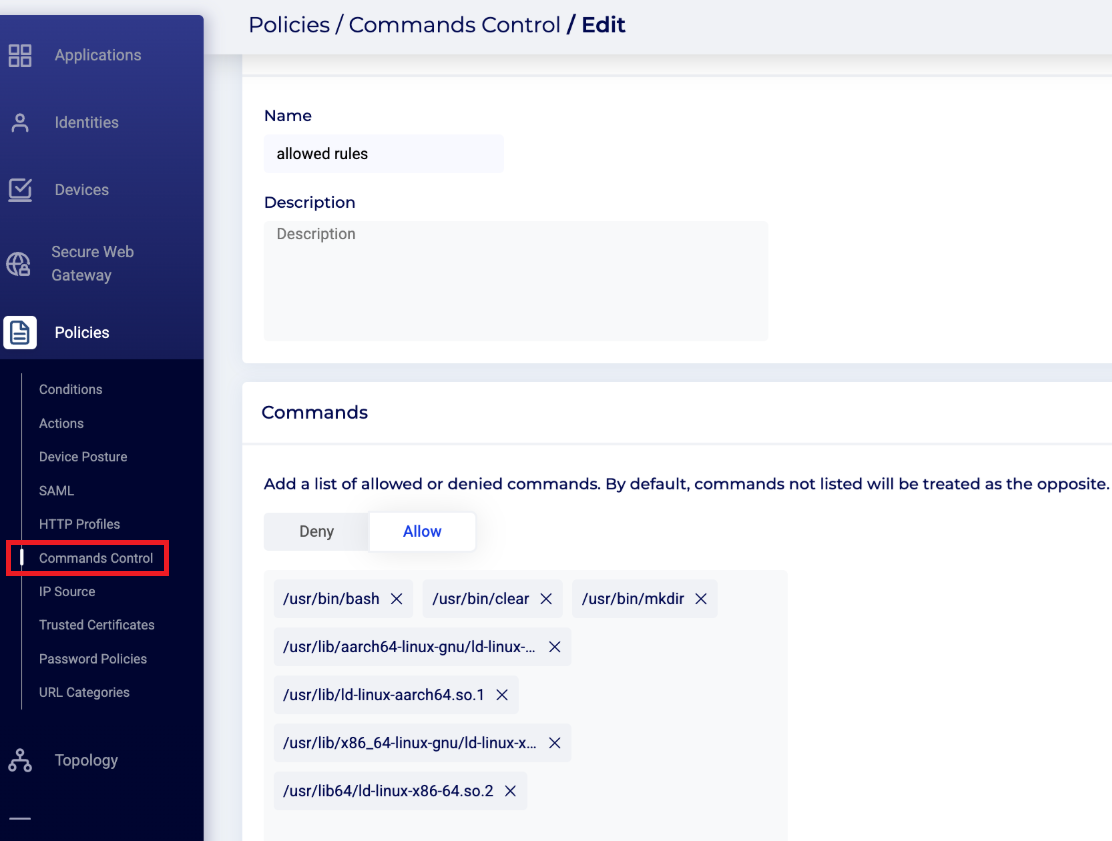
- To create a new policy with allowed rules and denied commands, go to the Policies > Commands Control page of the Cyolo admin portal.
- Create a Name and Description for the policy.
- Choose from the list of available allowed and denied commands at the bottom of the screen. Note that by default, commands not listed will be treated as the opposite.
- Once the policy is set, go to the Policies > Actions page, and select the relevant policy there.
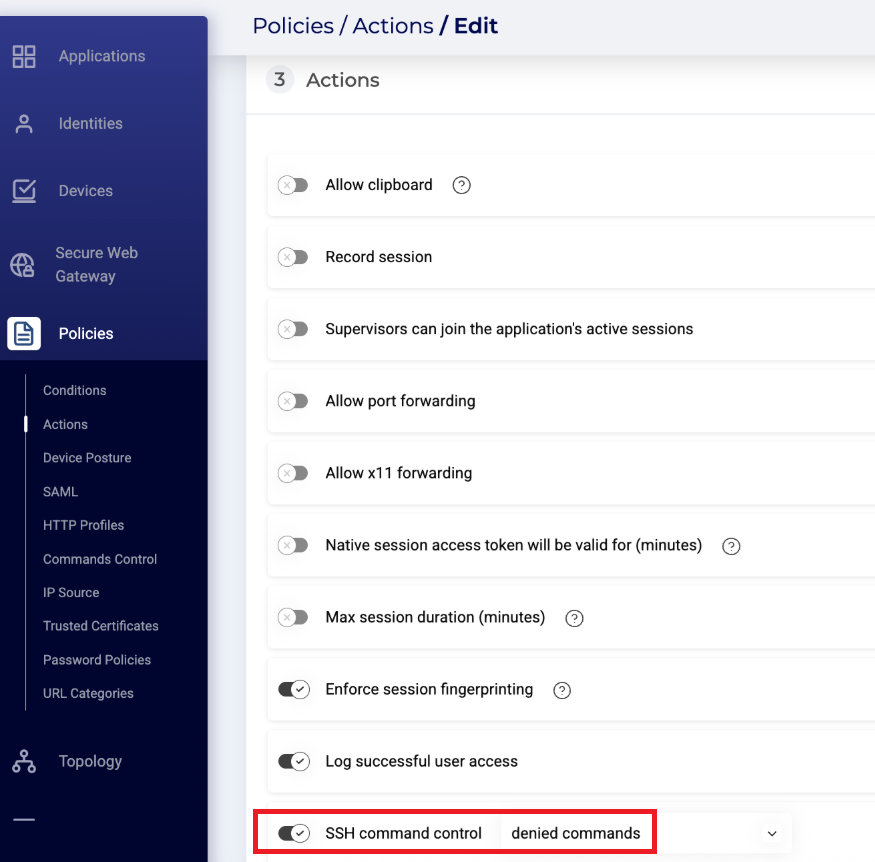
- See the SSH section of the Policy Actions page for additional information.
TBD - Clarifications on Command Control
Server requirements
The service uses a kernel api that was introduced in version 5.1.0.It should work on every distro with a kernel from that version and up, but installation from the idac is only supported for specific distros.The service was fully tested only on some distros.The service has rpm and deb packages. The idac will automatically detect Ubuntu, Debian, Rhel and Fedora systems and will install the service using the correct package.The service was fully tested on: Ubuntu 24.04, Debian 12 and Rhel 9, but should work on any of those distros' newer versions as well and might also work on older versions.
Installing the service:
Installation is done through the idac in the UI. Root credentials are needed and the server must allow root connection via ssh, for the duration of the installation.
All applications of the same server must use same instance of vault credentials for root.
Uninstalling the service can be done through the idac via api, and requires root connection. the api is https://<base-url>/manage_command_controlled_server/uninstall/<ip:port>.
A server that was previously installed can be reinstalled via the api as well with the api: https://<base-url>/manage_command_controlled_server/install/<ip:port>.
Supported linux distributions are debian/rhel-based, runnning on amd64 or arm64.
Configuring service in idac:
Creating a policy in command control:There are 2 modes of operation: “Allow list“ and “Block list“.When using “X list“ all commands in list will be Xed. The rest of the commands will be the opposite of X.Important note: When working in “allow“ mode, it is important to remember the system will block any command not in the list, including implicit commands and essential system commands. This also applies to library calls. This means, the admin will have to configure the system in a way that it can function. Usually this includes allowing at least a shell command (e.g. /usr/bin/bash) and a libc implementation, the exact required commands to be allowed may depend on the exact environment, here are some examples for common default paths:rhel-amd64: /usr/lib64/ld-linux-x86-64.so.2rhel-arm64: /usr/lib/ld-linux-aarch64.so.1debian-amd64: /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2debian-arm64: /usr/lib/aarch64-linux-gnu/ld-linux-aarch64.so.1After creating a command control policy, you can create an action policy and attach a command control policy to it.Then the command control policy can be attached to an ssh application.Note that you must check the “enable command control” checkbox for every application on the same server if you want the policy to be in effect, even if the service is already installed on the server.
Updated 6 days ago